DARK WEB AND APPLICATIONS TO USE DARK WEB
DARK WEB
Dark web is the
World Wide Web content that exists on darknets, overlay systems which use
public Internet yet we must particular software, configuration or approval to
use. Let’s see TOR and VPN Anonymous enough for Dark Web.
TOR BROWSER
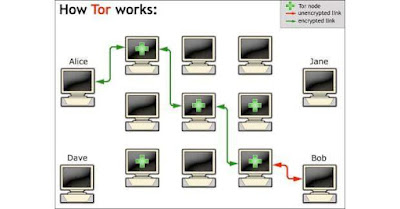
Tor browser
ensures you by bobbing your communication around an distributed system of
transfers keep running by volunteers all around the globe: it prevents some
person viewing your Internet connection from realising what websites you visit,
it prevents the websites you visit from learning your physical location, and it
gives you a chance to get to websites which are blocked.
TOR and VPN Anonymous enough for Dark Web
It is utilised by governments, writers, bloggers, whistle-blowers, additionally by drug dealers
who are offering unlawful medications at the alleged darknet markets.
At the point
when a client begins utilising Tor, it goes through the primary hub in the
circuit from a pool of 2500 out of 7000 PCs, which named as “Entry Guard” which
has high uptime and accessibility.
Despite the fact
that sooner or later, it has a track of the source of activity yet not what is
in it.Last hubs of circuits named as exit nodes where your information or
activity will be conveyed.
The middle
switch in the circuit goes about as Tor hubs to keep up an adjust of input and
output hub to exchange the information.
As the activity
goes from customer to leave hub in a scrambled state, attackers can’t read it.
Just packet
lengths, direction, size, time helps to show a user; this visiting technique
called as fingerprinting. A group of hackers who earlier hacked Play Station
Network and Xbox organise; after these assaults, the hacker group reported that
they are following Tor Network, which they considered an hard challenge.
Within a couple
of weeks hackers figured out to take control of 3000 routers, and they
uncovered beyond 95% of clients’ personalities!
Some proof
suggests that a lot of Tor hubs are being controlled by the NSA.
The way that
Tor’s leave nodes (routers) are having some security issues is likewise
conceded by the organisers of Tor system, and it was the principle motivation
behind why Agora, once a wellknown darknet showcase, has ceased their
operation.
This is a case
of what can happen in the event that you just depend only on Tor for secrecy on
the Deep Web.
VPN virtual private network
A virtual
private network (VPN) extends a private network across a public network, such
as the Internet. It enables users to send and receive data across shared or
public networks as if their computing devices were directly connected to the
private network.
TOR and VPN Anonymous enough for Dark Web
At the point
when utilising a VPN you associate with a server keep running by your VPN
supplier (a “VPN server”) with a encrypted association.
This implies all
information going between your PC and the VPN server is encoded so that
exclusive you and the VPN server can “see” it.
TOR and VPN can
be used effectively,give Tor a chance to Encrypt your connection towards the
VPN server first; from the VPN your connection comes back to Tor; then again to
the VPN and lastly to the Internet.
Along these way,
even your ISP has no clue that you are utilising a VPN, and your VPN supplier
likewise has no record of your exercises; your target site doesn’t have entry
to your exit hub and you have the highest level of security!
So, your
connection looks like this: Computer > Tor Encrypted VPN > Tor >
VPN > Internet
VPN Compatibility
Provides
complete support for Windows, Mac OSX, Android and iOS platforms. Many also
support Linux and Chrome OS (if only indirectly).
Support for
Blackberry OS and Windows Mobile devices, however, is much deficient.
Advantages
- VPN into a cost effective solution for organisations by utilising an uncommon system.
- Virtual private networks offer a higher level of secure communication when compared to other remote methods of communication.
- Have high levels of security, using a VPN connection users can surf safely, including through a WiFi hotspot. By using VPN users can access a computer or network from anywhere as long as there is internet connection.
Disadvantages
- Reliability can become a cause depending upon the service provider that you choose.
- The design and security implementation for a virtual private network can be complex.
- Speed is likely the greatest downside, particularly on the off chance that you live in territories where you have an awful connection as of now.



Comments
Post a Comment